For distribution with WASTE v1.5 beta 2
Original document (Documentation Revision 4) by: LANman
Revision 5 by: sHARD>> (sH4RD)
Revision 6 by: castleofmusic with editing by sHARD>> (sH4RD)
Main goals:
WASTE is a wonderful tool that can let you transfer personal files
between work and home safely. The WASTE software is released
under the GPL which allows free use and modification of the program but
explicitly
DISCLAIMS ANY WARRANTY and DOES NOT GUARANTEE the fitness of
the
software for any purpose. In normal language this means: What you do
with this setup & FAQ guide and with the software is your responsibility;
you accept any and all legal issues that may arise by reading this or
by using the software. If you use it for anything else than what it is
intended for --- that’s your problem.
WASTE in its current implementation is a distributed and
decentralized network of secure FTP-like servers. Users can share some
of their files and browse files that other users share. Users can
initiate transfers of files or whole directories, in either direction
(uploading to or downloading from other users), just like FTP. Finally,
users can chat to each other privately or in groups in
much the same way as when using AIM/ICQ/IRC/etc.
A WASTE network does not have a central server. All users can directly
connect to each other, unless one of them is behind a firewall which
blocks the port 1337. (This is the default port used by the WASTE
protocol.) In that case, the user who is behind the firewall can
initiate a connection to an open (not firewalled) WASTE host. Two
firewalled users can still connect to each other indirectly, i.e. by connecting to
other users who are not firewalled. Users connected indirectly through
other users can browse and exchange data in the same way as users
connected directly, because the WASTE system takes care of the routing
dynamically and transparently. Connections
between WASTE nodes persist even if some nodes have a dynamic IP.
All communications in the WASTE system (file transfers and chat
messages) are encrypted with a strong public key cryptography: 1024,
1536, 2048, 3072, and 4096-bit keys are supported. Unlike the standard
FTP procedure, WASTE users do not authenticate with passwords but
instead they exchange public keys and accept them, i.e. import
them into their WASTE profiles (keyrings). A WASTE user X
can directly connect to a WASTE user Y only if X's public key has been accepted
by the user Y. Every user is uniquely and securely authenticated on the
WASTE network, so a user can be sure that the identity of other users
is authentic.
To ease the growth of the network in case everyone trusts everyone else, there is also an option for accepting keys automatically: if A accepts B and B already accepted C, then the system can make A also accept the key of user C. This will happen only if A enables the option to "auto-accept" keys and if B enables the option to "rebroadcast" keys.
The WASTE network is entirely user-controlled: each user decides
whose public keys to accept, how many incoming and outgoing connections
are allowed, whether to allow unrequested incoming data, and what
bandwidth to allocate to the WASTE transfers. A WASTE user
can see all incoming and outgoing connections in real time. Particular
IP addresses
may be "banned" to prohibit connections, and particular data transfers
may be stopped.
An additional security/privacy feature is the "network password".
Each user can set the network password to any string and then other
users will not be able to connect to that user unless they also have
set the same network password. So this feature works as a filter among
WASTE users, effectively selecting a sub-network.
The current version of WASTE does not implement distributed
downloading, so each file is always downloaded from one specific user
and never from several users at once. So WASTE is not like traditional
p2p filesharing networks where you can search for files and download
them from anonymous users. WASTE is more like FTP where you know the
user who shares certain files. (Note:
you can browse and search
among all
files shared by all users. You can request a file search by entering a
search string in the top line of the Browser window, or in a Chat
window by entering e.g. "/search filename.txt".)
However, WASTE differs
also from FTP because it maintains a decentralized network where many
nodes are connected to each other indirectly (through other nodes), and
therefore the routing of a particular file transfer may change during
that transfer. Downloads and uploads will be automatically rerouted and
resumed if
some of the intermediate nodes are removed from the network, as long as
the connection can be maintained through remaining nodes. The latency
of a WASTE network (the time delay before starting a file transfer) is
usually much lower than when using a traditional p2p filesharing system.
WASTE is in some ways similar to but in other ways different from
edonkey-like p2p filesharing networks. You might want to study this
section before deciding whether WASTE is right for your needs.
Efficient distribution of large files that many people
want to download and share.
Quick and secure exchange of small quantities of data (e.g. much
smaller than a CD image) between specific users who know and trust each
other. It is thus a secure replacement for FTP, email attachments, ICQ
file transfers, or ssh/scp transfers.
waste-*-setup.exe
and run it (see http://waste.sf.net/ and get the latest version).
Follow the installer to get WASTE installed (it's easy -- just keep
clicking "Next"). Then run WASTE from your start menu because it does
not make a desktop icon for you. Alternatively, the WASTE executable (waste.exe)
can be copied by hand to any directory and run from there; the
executable does not require any DLLs beyond those present in Win98 or
later. When run, waste.exe will create and modify some
files in the same directory, so a WASTE installation cannot be put on a
read-only filesystem.
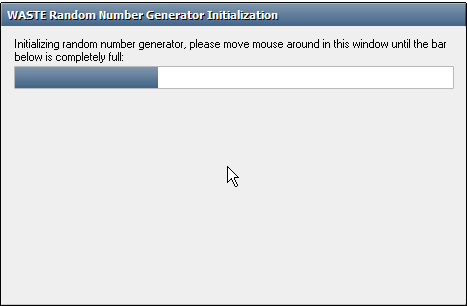
You should move your mouse all over the box in order to help generate better random numbers required by the program.
The following window will appear:
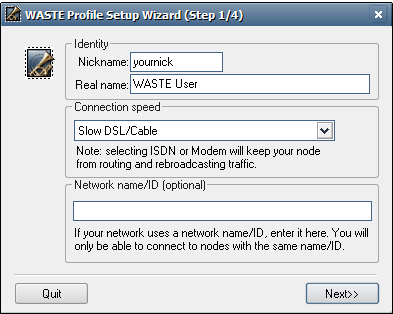
Type in your nickname;
use whatever nickname you want to use e.g. in a
chat room or in a forum. This will identify you informally to other
WASTE users. (You will
be able to change it later.)
"Real name" can be whatever you choose. It will be used to identify
you to other users when they request more information about you.
Set your connection speed to whatever best matches your Internet
connection. (This is only a guideline for the WASTE program and you
will be
able to fine-tune your bandwidth and network settings later.)
"Network name" is the "network password". Leave this blank for now unless you definitely know that you need it (see "Set up security features" below).
Click "Next>>".
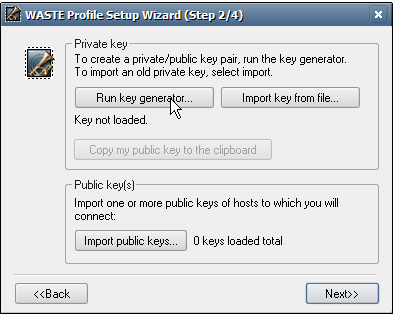
This starts the creation of the default profile. The
default
profile is stored
in files Default.pr0, Default.pr1 and so
on. (Note: You will be able to
create more profiles
later by pressing the button "Profile manager" in the
"Preferences/Profiles" dialog.)
The first step is to create a personal
key which is
your identity on the WASTE network. The key has the public and the
private parts. The
private part of the key is contained in the file Default.pr4
and you
must store that file safely! This file should remain secret and never be shared. (On the other
hand, the public part of the key should be freely distributed to people
who participate in the WASTE network, or else you will not be able to
connect to them.)
You can later generate more personal keys, store them in files, and
then reactivate ("import") personal keys you generated earlier. At any
time, as you are running a WASTE session, only one personal key can be
active. You can run different WASTE sessions in parallel with different
personal keys. (Thus in principle you can use several WASTE identities
at the same time.) You need at least one personal key now to start
working with WASTE.
Click on "Run key generator..." to generate your personal key.
The following window will appear:
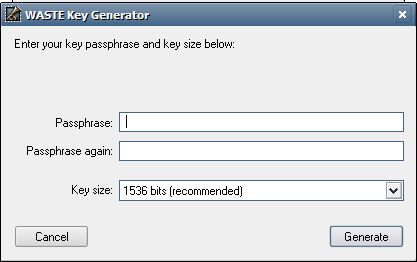
In this window you can choose the length of the key and the password
for the key.
The default length of the key (1536 bits) is sufficient for most applications. A larger key length will make your computer work harder when decrypting files.
The personal key has mandatory password
protection, so you must
choose a password. Use a mixture of letters, numbers, and special
characters that is difficult to guess, and at least 8 characters long.
Without that
password, the WASTE program cannot use your key to log you on to a
WASTE network. So a person who gains access to all your files but does
not know that password will not be able to
use your personal key. Choosing a short password or a password which is
an English word is a bad practice; this is most often the reason
passwords are cracked!
Note: You will have to enter
that password each time
you start the WASTE program, unless you choose the option to "store
your password" (this option will be available when you first start
WASTE with your key). The option to "store the password" is
insecure because the password will be stored in plaintext in the file
Default.pr0. If someone gets all your Default.pr*
files and if you also
selected the option to "store the password", then they will be able to
impersonate you on the WASTE network (i.e. use your personal WASTE
key).
This would be a breach of security and authentication; for instance,
the impersonator could receive your file transfers instead of you or
participate in your personal chat sessions.
Click "Generate".
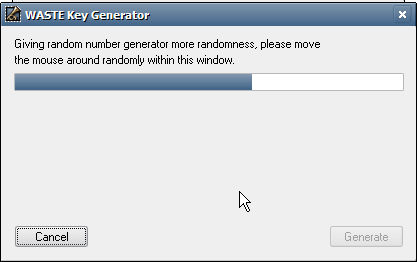
Move the mouse around until the "Generate" button is transformed into an "OK" button.
Click "OK". You will get back to the personal key window:

Now that your personal key has been generated, you should copy its
public part (your public key)
to the
clipboard using the button "Copy my public key to the clipboard". From
there, you should copy your public key to a file, an email message, a
public forum, or to any other such place from where you can send your
public key to other people. (Note:
Your public key is not stored in any Default.pr* file! If
you forget to copy it now, you can later go to "Preferences/Private
key" and press the same button "Copy my public key to the clipboard".)
Public keys should be exchanged in such a way as to assure
the identity of each person. For example, they can be posted in a forum
where users cannot edit other users' messages and where an
impersonator cannot easily flood the forum with fake public keys.
Alternatively, public keys can be exchanged at a personal meeting.
You should receive some public keys from other WASTE users and now
is a good time to import some of them into your WASTE keyring. (Your "keyring" is
the list of public keys of WASTE users whom you trust.) Those public
keys to be accepted
should be stored in one or more plain text files. (It is OK to paste
several public keys into one text file.) For convenience, select the .txt
extension for those text files. (You will always be able to accept more
public keys later, or to remove the keys you previously accepted.)

Select the text files containing the public keys, one by one. Alternatively, paste the public key text directly into the dialog box at the bottom of the window and click “Load key text”.
A message will appear telling you that public keys were imported.
Click "OK".
Click "Next>>". The following window will appear:
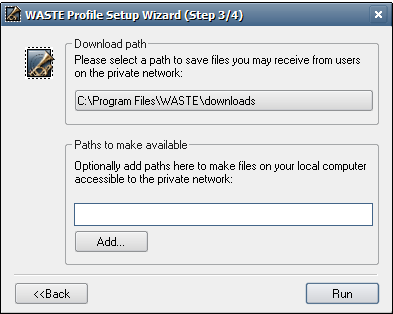
Here you can select a location to be used to store your downloads
and also optionally select the
folders you wish to share on the WASTE network. Note that
multiple shared folders may be added by clicking the "Add" button or by
editing the semicolon-separated list of directories by hand. The
default values are OK since you will always be able to change these
settings later.
The basic setup is finished. Click "Run" to run the WASTE program.
You will see a blank window showing 0 connections ("network down"). You
can now continue with the configuration of WASTE. In the main window,
click "File/Preferences" and explore the various settings found there.
The WASTE network may use a "network password"
(entered in Preferences/Network/Password) for added security. If you
enter a network password in that dialog box, WASTE won't allow other
users to connect to you unless they have the same network password,
even if their keys are in your keyring. The network password (if
entered) is always stored in
plaintext in the file Default.pr0, so it only needs to be
entered
once.
Note: The network password
is also called "Network name/ID" in
that dialog box. There are no separate "Network name" and "Network
password"! Both are the same thing in WASTE, and it would be better if
the wording were consistent and the network password were never
referred to as "Network name/ID".
If you are using the network password, it is recommended to check
"Activate stealth mode". (Preferences/Network/Password)
The "stealth mode" is more secure.
It is necessary for you to
use the stealth mode if other WASTE hosts are using it.
It is recommended to uncheck the options "Auto-accept public keys" and
"Automatic
rebroadcast public keys"! (see Preferences/Network/Pending keys) These
options are dangerous because the network may grow uncontrollably by
extending the trust too far. For example: A trusts B, B trusts C, but A
may not trust C; with the automatic broadcasting and acceptance of
public keys, A's distrust of C cannot be enforced since C's key will be
automatically broadcast by B and accepted by A. (Please note: even if A
does not accept C's key, the user C will still be able to connect to A indirectly through B.)
Think whether you want to enable the option to "allow my nickname to
be associated to transfers" (Preferences/File transfers). If your
nickname shows and you are trusted, people might be more tolerant of
your downloads. On the other hand, it decreases your anonymity because
it becomes known to the other person who is transferring the file.
(This is probably irrelevant at the current stage of the development of
WASTE because the current protocol broadcasts file transfer requests to
all users, so all participants in the WASTE network are in principle
able to deduce who is downloading what. This may change in a future
version.)
The important step is to select the maximum bandwidth you are ready
to use (see
Preferences/Network/Bandwidth). Note that once you connect, other WASTE
users may be able to send you arbitrary files and you also may be
able to send them files; this is just like FTP. (Note: There are
options to prohibit reception of unrequested files or to require a
manual confirmation.) Also, WASTE may route traffic through you to let
other users exchange data. So it is important to limit the bandwidth
right
away to a value you can live with. It is probably the safest option to
limit the total bandwidth
(not the per-host bandwidth) unless you are
on a really fast connection.
In the Preferences/Network window, you should choose whether you
allow network traffic to be routed through your WASTE node. (It is a
good idea to allow that because it will make the WASTE network more
robust.) You can also specify the maximum number of incoming
connections you accept and the port your machine will listen on
(default is 1337). The "Connection speed" setting is a guideline for
WASTE to load-balance the traffic.
In the Preferences/Profiles window, you can set the location of the
log file; it is useful if you plan to run WASTE unattended and examine
log files. The logging level of 1 will list only the IP addresses of
directly connected hosts; the logging level 4 includes messages that
explain why connections were not established; the logging level 5
includes also some debug messages.
Default.pr3 in plain text and it is completely
safe to distribute that file to other people.)Default.pr0)The entire configuration is saved in the plain text files Default.pr*
and WASTE.INI which are kept in the same directory as
waste.exe. Once you successfully set up WASTE and have connected
to some hosts, quit WASTE (it needs to save settings on exit) and make
a backup of all configuration files. It is especially important to back
up the private key because if you
lose it you will definitely not be able to restore it!
WASTE is a Win32 application which works well under the free
emulator Wine. Running WASTE under Linux/Wine is no different from
running WASTE under real Windows; the GUI may show some visual problems
but is otherwise fully functional. Here is a short overview of setting
up WASTE under Linux/Wine.
The usual procedure creates a $HOME/.wine/fake_windows/ directory,
this will be
your "disk C:" under Windows. Run the WASTE setup if necessary, e.g.
copy the file waste-setup.exe into $HOME/.wine/fake_windows/ and
run
> wine 'c:\waste-setup.exe'
Alternatively, you can copy the executable file waste.exe
and the profile settings Default.pr* from a
Windows machine.
Assuming the default location of the WASTE executable, run:
> wine 'c:\Program Files\WASTE\WASTE.exe'
The following problems with Wine/WASTE are found so far:
1) WASTE likes to remember exact window positions in its profile
(Default.pr0), however, this conflicts with some X window
managers that
assign some other positions to windows when you switch between virtual
desktops. The result: some or all of the Wine/WASTE windows disappear
when you switch to another virtual desktop and then switch back.
Solution: use the Wine configuration option to disable window
management. In the file ~/.wine/config, write something like
; Allow the window manager to manage created windows
"Managed" = "N"
Then all Wine/WASTE windows will appear inside one big black window and
there are no problems with disappearing windows.
2) The WASTE user interface generates some Wine warnings about missing
DLL functions. I put the following into ~/.wine/config:
[AppDefaults\\WASTE.exe\\DllOverrides]
"msvcrt" = "native"
"riched20.dll" = "native"
"riched32.dll" = "native"
"user32.dll" = "native"
"shell32.dll" = "native"
and then I copied the above listed Windows DLL files from a Win98
machine to the ~/.wine/fake_windows/Program files/WASTE/ directory. (I
guess they can also go to windows/system but I didn't try that.) The
main WASTE functionality seems to be fine even without these DLLs, but
chat and its flashing windows seem to be more problematic.
3) After switching to another virtual screen and back, sometimes the
Wine/WASTE window cannot accept any keyboard input and just beeps.
(This happens most often in chat windows because they are the ones that
use the keyboard input, but the same thing happens in all Wine/WASTE
windows that read the keyboard.) The cause of this is unknown. Usually
after one more switching of virtual screens the problem goes away.
(If you persist trying to get keyboard input, WASTE might crash Wine.)
4) There seems to be no way to type 8-bit characters or Unicode
characters into Wine/WASTE.
However, any 8-bit ASCII can be used in
network passwords or in personal key passwords. This may pose a problem
if you want to use the same WASTE configuration under Windows and under
Wine, and if you used 8-bit letters in your personal key password
and/or in the network password.
A workaround for entering passwords in high ASCII under Wine/WASTE:
first, input some wrong
passwords using Latin
letters, quit WASTE (this will save settings and close the files), then
edit the file Default.pr0 with a text editor that can
handle 8-bit characters, find the fields "networkname" and "keypass"
and
edit them to correct values. Then start Wine/WASTE again. (Note: You will need the option to "store the
password" or else the system will keep
asking you for the password each time you start WASTE! The network
password is always stored.)
5) There is a set of options in WASTE that has to do with the flashing
of windows (see Preferences/Chat/Windows). It seems that Wine/WASTE is
more stable (when using chat) if flashing is disabled.
6) Wine refuses to read links to directories (it reads only links to
files). This is to prevent Windows programs from entering an infinite
loop when trying to get a recursive listing of a subdirectory which is
linked to its parent directory.
The WASTE program opens the main window and some auxiliary windows.
The main WASTE window looks like this:
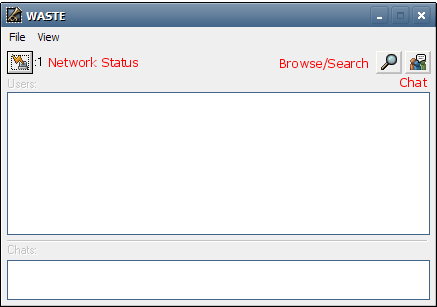
Press buttons to show the Network Status window (monitor
connections) and the Browser window (search for files). Press the Chat
button to create or join a chat room. These and other functions (e.g.
to display the Transfers window) are also available from the View menu.
The File menu can be used to display the Preferences window.
The bottom of the main WASTE window shows a list of the visible chat
rooms. Visible room names start with #, invisible ones start with
&. There is also a special room named $$broadcast
which goes to every connected user. A visible room will appear in the
following form: #wanparty -- double-click on it to join
that room. An invisible room will need to be typed in manually from the
chat
button, for example: &hidden (you must know its exact
name).
The "Network Status" window is used to connect to new hosts and to monitor the currently established direct connections to other WASTE hosts.
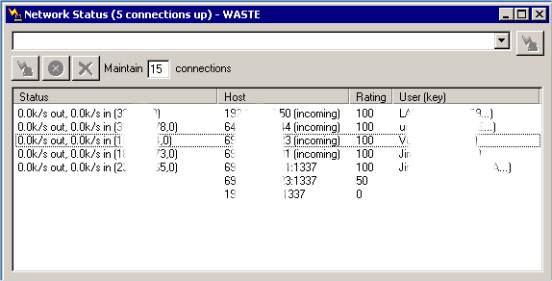
In the top field, you can enter the IP address or the hostname of the
WASTE host to which you wish to connect. That field is a drop-down
listbox which remembers all IP addresses you typed in, even after you
quit WASTE, so that next time you don't have to type these addresses
again.
Maintain connections: the number of connections your WASTE client will try to maintain. The number you should maintain will vary, think about the number of people that you want to stay connected to. On larger networks you most likely will not need to maintain a connection to everyone (this will be something that you will have to play with). Keep in mind: the more connections you keep up, the more of your bandwidth will be used for routing other people's connections.
For each connection, some information is displayed.
- Status: bytes per second sent ("out") and received ("in")
- Host: IP Address and port used by the remote WASTE host. The suffix "(incoming)"
means you are acting as server in that connection.
- Rating: The rating tells you how good a connection you have to
that host. A rating of 100 means you are directly connected to them. If
it is less than that then you are having connection problems. Every
time your WASTE program fails to connect to that host, it will decrease
the rating until it comes down to 0, then it will stop
trying to connect to that host.
- User (key): Username and the key signature of that user's public key.
The following window shows what happens when you right-click on a user's nickname, either in the main window or in the file browser:
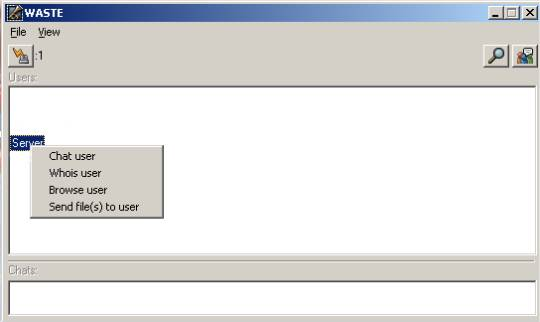
You will get a choice: to browse that user's files, to chat
privately to that user, to do a "whois" request for
more info about that user, or to send files directly to that user.
The Transfers window is displayed by selecting the "Show transfers"
menu in the main window, menu item "View":
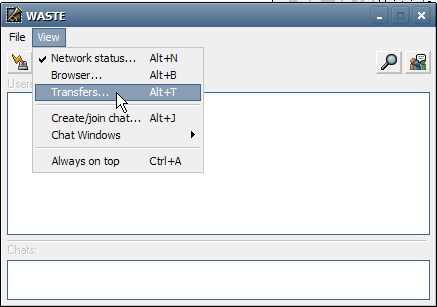
In the Transfers window you will see your downloads currently in
progress, the queued downloads, and the uploads currently in progress.
You will see the average kb/sec rate and sometimes also the nickname of
the user who is receiving or sending data.
The Browser window looks like this:
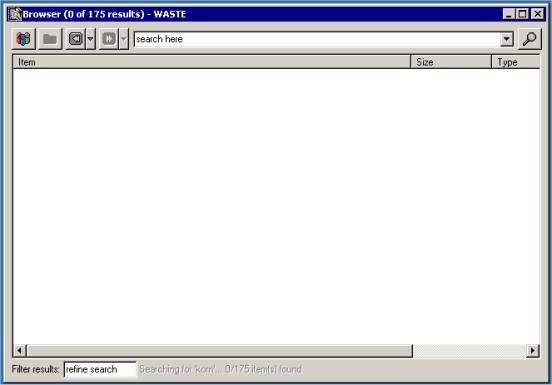
You can press on the left button to go to the top level where you
see the list of all users who have something to share. (The same can be
found by ascending up the directories.)
The top dialog box can be used to enter search parameters (press
Enter there): The WASTE program will search through all files shared by
all users and will display the search results in the box directly below.
To refine your search, enter a mask in the "filter results" box
after you have done a search.
The configuration of the WASTE session is performed through the
Preferences window:

About: Program information & version number.
License: View the GNU GPL.
Profiles: A profile is a complete WASTE setup (all configuration settings, private key, keyring, IP addresses of hosts, etc.) You can have several profiles which can be useful if you are using the program to connect to different WASTE networks, or if you want to have several WASTE identities, or if you aren't the only person using the program on your system. (Tip: don’t share your WASTE identity with someone else who is also using your computer! Keep your password private!)
Identity: The nickname everyone will see in WASTE, you can set this
to whatever you like but don’t leave it blank. The "Client ID" is the
unique code that identifies your WASTE client on the network. It is
generated at the beginning of the WASTE setup. If it is changed
afterwards, other users might have to reconnect to you.
Network:
Connection speed: This is a guideline to help WASTE load-balance the
network. Set this to something that best matches your connection speed.
Route traffic: If checked, your WASTE host will route traffic to other
hosts. If you don’t have port 1337 open or you have no way of
allowing incoming connections, then uncheck this or you could cause
problems
when other clients try to download files or connect to people.
Listen on port: This is the port on which your WASTE node will listen
to incoming connections. Leave this at 1337 unless everyone on your
network has
decided on a different port.
Advertise port on private network: This is important if you want others
to connect to you, WASTE will broadcast the fact that you can accept
connections. This feature is the key to WASTE and its ability to form a
strong P2P network.
Network Submenu:
· Password: Specify your network password.
· Private Key: If you ever need to regenerate a new personal
key, this is where you do it. It also gives you
easy access to your public key so you can copy it and send it to
others. The same window shows your key signature (a short hexadecimal
string that can be used to quickly verify the key; no two different
keys have the same signature).
· Public Keys: This is your keyring where all your accepted keys are kept.
· Pending Keys: If you wish not to accept new public keys
automatically, then this window will show all public keys which have
been broadcasted to you and await your
approval. It is recommended to uncheck the "re-broadcast" and
"auto-accept" options.
· Access control: Optionally, you can build a list of IP
addresses which you disallow.
· Your IP address: This is best to keep on "automatic".
· Bandwidth: You will want to manage the amount of bandwidth
is used. Inbound for download speed, and outbound for uploads. For
example, you might set the full
speed at night but only 1/3 of the full speed during the day. This
might be
important for some users because some ISPs don’t like it when you
download/upload more
than 6 GB of data.
- Limit incoming in kb/sec (I.E. downloads – 768k DSL – 60k to 70K max
- Limit outgoing in kb/sec (I.E. uploads – 384 DSL – 30k to 40k max
Be sure that these settings are not too high because it will consume
your internet connection very easily.
Connection saturation: If you enable this it will be constantly
blasting random noise data whenever you are not downloading or
uploading
files (but it will eat up your entire internet connection and that of
the users you connect to). Use the connection saturation with EXTREME
CAUTION!
Display:
How WASTE windows are displayed, whether to hide them to the system
tray etc.
Chat:
All chat options.
Perform: you can enter chat commands like “/join
#wanparty” to be executed each time you run WASTE, so that you can join
some chat rooms automatically.
Windows: Adjust window flashing, etc.
Logging: Enable logging of chat sessions.
File Transfers:
You can set “Allow my nickname to be associated with file
transfers” so people will know who is downloading from them.
It is recommended to check the boxes "Allow direct connections" and
"Try to establish direct connections". If you don’t do this, there will
be a lot of unneeded data
transfer through other WASTE nodes. However, if traffic is not a
problem, you can uncheck these boxes for added security, because
someone who is trying to
monitor your downloads will be confused by your data going through many
other WASTE nodes.
File Transfer Submenu:
· Receiving:
Download folder: You can set your download folder anywhere you like,
just make sure it's not the same folder that some other P2P client is
using or would default to. (This will cause a problem with your
partial downloads that might get shared.)
"Allow others to send me files": It is up to you whether you want to allow others to send you files. It is recommended to enable this option. You can always check "prompt before accepting" to set this feature to manual. (For unknown files & downloads, if you are using Windows as your main system -- be sure to always have antivirus software running!)
Limit downloads: Try to limit your downloads to around 4 because you
don’t want to pull to many files at the same time (it could saturate
your connections and slow down the transfers).
Use paths: This can be handy if you are downloading all files in a folder and if you wish to keep the directory structure after it's downloaded. You will have to adjust this accordingly.
· Sending:
File limit: Limit the number of file requests (default is fine).
Index files, allow searching and browsing: Make sure these are
checked! If not, nobody will be able to see the files you are sharing.
Directories to scan: This should be obvious, add the list of folders you wish to share out. Keep in mind that if you share out a drive (I.E. C:\) you also share out everything on that drive.
Rescans & cache file list: The option to rescan your directories every X amount of seconds may be useful to you only if new files are added before you have a chance to close and reopen WASTE to update file lists (e.g. if WASTE is running unattended for a long time). Set the delay to a few hours to avoid excessive disk usage while rescanning files. Note: WASTE does not update your file list unless you restart it or have this option set.
Make sure “cache file list…” is enabled, or it will have to completely re-index all your files each time you run it.A connection between WASTE nodes A and B is always directed: one node
initiates the connection and the other responds. Let us assume that the
node A initiates and the node B responds, then in this transaction A is
the client and B is the server. In the "Network status" window, B will
see a connection to A with the remark "(incoming)" which indicates that
B is acting as a server in that transaction. The node B, upon receiving
an incoming connection from A, will usually automatically attempt to
initiate a reciprocal connection to A. In that connection (if
successfully established), the node B will be the client and the node A
the server. This pair of connections is redundant: in fact, one
connection between A and B (in either direction) is sufficient for all
data transfers. The redundancy is intended to make the network more
robust.
Suppose two WASTE users want to exchange data. If one of them is
firewalled and the other is not, they can establish a direct connection
and transfer data in both directions without using a third WASTE node.
If both WASTE users are behind a firewall, they need a third WASTE node
which is un-firewalled, and then all traffic will go through that third
node. This potentially creates a network overload unless the firewalled
nodes are less than about 30% of all nodes. WASTE uses only one port
(1337 by default), so perhaps a firewall can be configured to let this
one port through. The port can be configured to other than 1337 (say,
to 80) in the WASTE program.
Note: WASTE currently cannot use a proxy connection.
This situation is not easy to deal with. First, you should remove
the
public key of X from your WASTE keyring. Then the user X will not be
able to connect to you directly.
However, X will be able to connect
to you indirectly, i.e.
through some other user Z if you trust Z and
if Z trusts X. In that case, all traffic between you and X will be
routed through Z and you will only see a direct connection to Z. If you
do not trust Z but you trust W who trusts Z, the chain "You <-> W
<-> Z <-> X" will still hold and the user X will still be
able to browse and download your files or to send you messages.
Therefore, to exclude the user X completely from a WASTE network where
everyone else trusts each other, X's public key needs to be removed
from the keyrings of every user
in the network. This is a perhaps unfortunate side effect of the mutual
trust scheme used in WASTE which may create difficult social
situations.
This is not completely clear at the moment. On the one hand, all
data
transfers are encrypted, so a third-party opponent will be unable to
determine the transferred content. However, due to the current weakness
of the protocol, an opponent whose public key is approved by someone on
the
network is automatically a party of the WASTE communications and can
sniff other people's traffic (such as filenames in file requests and
all chat messages). This problem may be addressed in a future release
of WASTE.
The IP addresses of participants can be seen only with a direct
connection between WASTE nodes. In other words, only the people whose
public keys I approved will be able to know my real IP address; all
other users will merely see my nickname and my shared files.
There is also the "stealth mode" (activated from
Preferences/Network/Password), and the tooltip documentation says that
WASTE becomes "more difficult to detect" -- in other words, an ISP who
wants to prohibit WASTE will have a harder time.
There must be at least one permanent node with either a fixed IP
address or a fixed hostname (e.g. *.dyndns.org). The holders of these
nodes should authorize your key. Type the address or the hostname of a
permanent node into the field at top of the "Network browser" window
and press the button next to that field. In a little while, a
connection should appear with some kb/sec rates. You should also
authorize the public keys of other nodes (only of those you trust, of
course).
If the connection does not appear, either your public key was not
approved, or there are perhaps some problems with firewalls, maybe an
incompatible version of the WASTE software, or the remote node already
has the maximum number of incoming connections, or you entered an
incorrect network password.
You can choose your maximum upload and download speeds, either total
or
per-connection. Since the WASTE system determines the routing
dynamically (so the routing can change even within the duration of one
file transfer), the speed will vary somewhat, but usually will be
approximately constant and equal to the limit you set or to the network
capacity. Encryption does not slow down file transfers.
Before you run off to worry about your encryption key sizes, keep in mind that it is typically much easier to break in and recover a private key than it is to crack/factor it. So be sure to keep your keys safe and your systems secure!
In order for someone to join your network they first need to be
given your public key and the IP address or hostname of some WASTE node
that
accepts incoming connections. (All nodes accept incoming connections
unless they are configured not to accept them, or unless they are
behind a firewall.) The WASTE node should also have approved the public
key of the new node.
Once the new node connects to an existing node, it will see all other
connected users -- the list of visible users is shown in the main
WASTE
window. Note: the browser
window shows only the list of users who share some
files).
The more nodes that accept connections, the stronger the mesh will be
and the less load that will be put on the network. This network is
designed to be in a mesh topology, not a star topology. The
connection graph typically looks like a random redundant mesh of
connections. Here is an example:
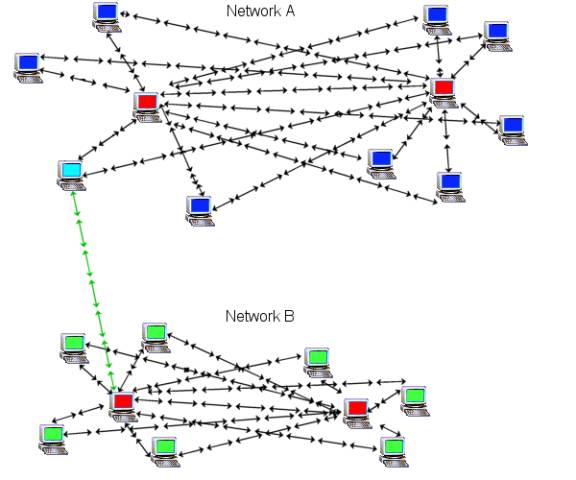
· The red computers are WASTE nodes that have the port 1337 open. Other WASTE clients have connected to their IP address directly. You are part of network A.
· The blue computers are WASTE clients that have not opened port 1337 or cannot open any incoming ports. In some cases you may have an Internet connection that does not allow incoming connections, such as an Internet connection that has N.A.T. running at the ISP level. If this is the case the only way around it is to get a static IP and that can cost lots of $$$.
· The light blue computer is part of your existing network but may also connect to a computer in another network (lower part of the graph). If that computer connects to anyone in the lower part of the graph, then the entire lower part would merge with your network. Now there is nothing wrong with adding more WASTE clients to your network, but you may not trust the rest of their clients.
File browsing – allows users to browse a virtual directory structure for each user on the network. Each user can specify a list of directories to make available to other users on the network. You can browse individual users by right clicking on some ones name listed in the main window and select browse.
"How do I search?"
You can search from any chat window with "/search movieclip.avi", or
you may search from the Browser Window (Alt-B). The top section that
shows the Path you are browsed to is also a search window.
“How do you chat?”
This feature is primarily accessed through the main WASTE window. You can click on the create/join chat button and create a new room or type in a know room name. If some one already has a chat room created it will show at the bottom of the screen. To PM some one just right click on their name and click chat user. Also to join the same chat room each time you open WASTE type in "/join #wanparty" in the Chat: Perform: window.
“Why do I only have one connection and/or people can’t connect to me?”
WASTE is meant to distribute network connections; after your client makes a connection to anyone that is part of the network WASTE then broadcasts your IP-address out to everyone that is currently connected. This function of WASTE works great, but with DSL routers performing N.A.T. you end up having a fake IP-address on the system running WASTE. Then your client connects to a WASTE network and your fake IP-address is broadcasted to everyone that is part of the network and then no one can connect to you because the wrong IP-address is being sent out. This is also the reason that if you check your network connections there are a lot of IP-address that you keep trying to connect to but can’t.
“Well then how do I setup WASTE so it will allow people to connect to me?”
In order for WASTE to work it needs to have as many people with port 1337 open and their “real” IP-address broadcasted out as possible so if one of the hosts are offline then the entire network will not go down. As of version 1.3C of WASTE it has no way of telling if the IP-address of the system that WASTE is on is your real IP-address, but there is a way around this. You need a service that updates your IP-address to a DNS server; that way your personal DNS address (I.E. mydns.dtdns.net) will point to your current IP-address (The IP that your ISP gives you I.E. 66.143.98.23).
“Port 1337 huh?”
Yep that’s that standard TCP/IP port that WASTE talks on. To open it you need you go into your router or firewall software and do a port forward (port 1337 to 1337 with both UDP and TCP enabled for that port) to your fake internal IP-address. The IP-address you set your port forward to needs to be a static IP-address, because the IP-address you have now may not be the one you have tomorrow with DHCP. Now I am not saying you should not run DHCP you just need to manually set an IP to the system that is running WASTE. Depending on what OS you are running the way to see what network settings your DHCP server has given you can differ. After getting your settings (I.E. IP block 192.168.0.***), subnet mask, default gateway, and your DNS servers) you can pick an IP-address that’s much higher up than what you have now (like if your using .3 or .5 or even .100s) like IP-address .200 should be safe for most. You can really use any address you want just make sure your DHCP server is not going to give it out (for most people you will never use more than 10 IP-addresses).
“Ok how do I setup a DNS service now?”
First you need to sign-up for a dynamic DNS service to forward your IP-address to a DNS server. Then you need to find a DNS updating client that will work with your DNS service. The web site you get your service from will have a list of clients with various features; you may need to try a few clients in to find the one that works for you. IF your running Windows NT, 2000 or XP try to get a version that runs the DNS updating client as a service so it can run in the background. You need to leave the service running all the time so it can update your IP-address as it needs to, don’t worry it uses very little system resources and very little bandwidth.
“Where can I find such a service?”
Well just about anywhere on the Internet, a google search for an IP poster, dynamic DNS, or DNS hosting will get you some kind of service that will do the job. Here are a few options for that you can try:
http://www.ddns.net/services/page/free/dynamic/dns
This is a good fee service but the web site has adds.
This is my preferred service, it lets you update your IP every 10 min. but it costs a one-time fee of $5.
http://www.dyndns.org/account/create.html
This is another good free service but they only let you update your IP-address every few hours.
“Now I am ready to share files, connect to others, and have others connect to me what now?”
Ok in your WASTE client go under: File: Preferences: Network: IP-address: check the force incoming IP to:
Type in your DNS address (I.E. mydns.dtdns.net) then WASTE will send out your real IP-address and not your fake one, now after you connect to someone are they connect to you your real IP will now be broadcasted out and everyone on the network will be able to connect to you. The great part about WASTE is after you have connected to someone or if someone broadcasted their IP to you it keeps that address in WASTE connections and allows you to quickly reconnect with them in the future.
“Can I or the network be hacked into?”
It is important to remember: All encrypted messages can be cracked through brute force cracking! This can take quite some time, depending on the key length (upward of 900 years with some). Other attacks use known weaknesses in an algorithm that can be very complicated and confusing to comprehend. Weak keys are the number one cause of these systems getting compromised. The size of the key determines the amount of time it will take. They capture the message and then begin guessing as to what the key could be. The guessing is done by some kind of brute force program and the guesses are every possible key that the key could be. They figure out the algorithm used, what the key length is, and then go at it.
“Ok I goofed and gave out my key to some one I don’t trust and I think that myself and the others that are part of my network could be in danger, what now?”
Chances are you are being paranoid, the RIAA or the movie moguls are after the 4+ million file sharing people on open P2P networks not you and your (at most 50) friends. What you will need to do is go into Preferences: Private key: and then generate a new pair of private and public keys WITH A NEW PASSWORD. Having a new key (and a long one) is very important; make sure it is not like the old one. You will also have to have every one else do this as well and then re-exchange your public keys.
“What network name/ID should I use? Or should I even use it?”
A network name can be useful for example, your WASTE network could grow way to large and go past the intended limit or you have accidentally merged with another WASTE network and you wish to split up your networks. After you have chosen a network ID anyone that does not have it set the exact way (case sensitive) you do will not be able to join your network or even see you (even if they have your IP-address AND you have shared keys). Your WASTE client and every one else’s will simply ignore them. You can set a network name/ID at the time of install or later under preferences.
“I can’t open my firewall up or I can’t run a DNS service, can I still partake in the WASTE network?”
Due to the way this network works, you do not HAVE to. Also keep in mind that if there are to many people on you network with out port 1337 with some way to connect to them it will create a weak network, and if your only connection goes down- you all do. People can download files from you via your existing outbound connections to other servers. Every WASTE network requires a least ONE node that allows access to port 1337 and a way to get their updated IP-address.
“Should I save my password when I open WASTE?”
The only problem with a long password/key is that it hard to remember, the paranoid part me says “No! Don’t save your password” but you will have to use your best judgment for saving passwords (I.E. a family computer, public computer, your company’s computer, or if you share your computer). REMEMBER the weakest link is always the person that is careless about his/her security.
Since WASTE requires a small trusted network to function efficiently, it benefits greatly from cryptography. Using public-key encryption for session key negotiation and user authentication allows both the prevention of unknown users from joining the network as well link data security to prevent unknown users from “sniffing” network traffic.
WASTE also provides for an additional “network name or ID” that can be used to secure a network against people who do not have the name or ID. This can be useful if you wish to easily prevent multiple networks from merging, or change it to easily remove access of user(s) without having to make everybody ban those user(s) public keys.
WASTE uses a (hopefully) cryptographically secure random number generator based on the implementation in the RSA reference code. The code uses a 32 byte state, with 16 bytes of counter and 16 bytes of system entropy constantly mixed in, and produces random values by using MD5.
WASTE connections use RSA (with 1024 bit or greater public key sizes) for exchange of 56 byte Blowfish session keys, and 8 byte PCBC initialization vectors.
The link connection negotiation, where A is connecting to B, goes something like this:
1. A sends B 16 random bytes (randA), or
blowFish(SHA(netname),randA) if a network name is used.
2. A sends B blowFish(randA, 20 byte SHA-1 of public key + 4 pad bytes).
3. B decrypts to get the SHA-1 of A’s public key.
4. If B does not know the public key hash sent to it, B disconnects.
5. B sends A 16 random bytes (randB), or blowFish(SHA(netname),randB)
if a network name is used.
6. B sends A blowFish(randB,20 byte SHA-1 of public key + 4 pad bytes).
7. A decrypts to get the SHA-1 of B’s public key.
8. If A does not know the public key hash sent to it, A disconnects.
9. A looks up B’s public key hash in A’s local database to find B’s
public key (pubkey_B).
10. A generates sKeyA, which is 64 random bytes.
11. If a network name is used, A encrypts the first 56 bytes of sKeyA
using the SHA-1 of the network name, to produce EsKeyA. Otherwise,
EsKeyA is equal to sKeyA.
12. A sends B: RSA(pubkey_B,EsKeyA + randB) (+ = concatenated).
13. B looks up A’s public key hash in B’s local database to find A’s
public key (pubkey_A).
14. B generates sKeyB, which is 64 random bytes.
15. If a network name is used, B encrypts the first 56 bytes of sKeyB
using the SHA-1 of the network name, to produce EsKeyB. Otherwise,
EsKeyB is equal to sKeyB.
16. B sends A: RSA(pubKey_A, EsKeyB + randA), (+ = concatenated).
17. A decrypts using A’s private key, and verifies that the last 16
bytes are equal to randA.
18. B decrypts using B’s private key, and verifies that the last 16
bytes are equal to randB
19. If a network name is used, A decrypts the first 56 bytes of sKeyB
using the SHA-1 of the network name.
20. If a network name is used, B decrypts the first 56 bytes of sKeyA
using the SHA-1 of the network name.
21. Both A and B check to make sure that the first 56 bytes of sKeyA
does not equal the first 56 bytes of sKeyB. If they do (which is
statistically unrealistic and would lead one to believe it is an
attack), they disconnect.
22. Both A and B check to make sure the final 8 bytes of sKeyA differs
from the final 8 bytes of sKeyB. If they are equal, disconnect.
23. A uses the first 56 bytes of sKeyA XOR sKeyB to initialize Blowfish
for send and receive. A uses the final 8 bytes of sKeyA as the PCBC IV
for send, and the final 8 bytes of sKeyB as the PCBC IV for receive.
24. B uses the first 56 bytes of sKeyA XOR sKeyB to intialize Blowfish
for send and receive. B uses the final 8 bytes of sKeyB as the PCBC IV
for send, and the final 8 bytes of sKeyA as the PCBC IV for receive.
25. All further communications in both directions are encrypted using
the initialized Blowfish keys and PCBC IVs.
26. A sends B the constant 16 byte signature (“MUGWHUMPJISMSYN2”)
27. B decrypts verifies the signature
28. B sends A the constant 16 byte signature (“MUGWHUMPJISMSYN2”)
29. A decrypts and verifies the signature
30. Message communication begins (each message uses a MD5 to detect
tampering – if detected, connection is dropped).
The quiet launch of WASTE was the work of Nullsoft's principal developer, Justin Frankel, a soft-spoken 20-something known for his tech savvy and his streak of rebelliousness.
He released his latest project, WASTE, onto the Nullsoft site on May 28, 2003; and it quickly became big news. The software gets its name from Thomas Pynchon’s The Crying of Lot 49, an is an acronym for “We Await Silent Trystero’s Empire.” W.A.S.T.E. is an underground postal system in the novel. Frankel’s WASTE got mentioned on Slashdot and on Daypop and a lot of people managed to download it before it was taken offline.
WASTE had been used internally to share files between AOL's San Francisco office, where Nullsoft is based, and its Dulles, Va., headquarters, according to Ian Rogers, a former founding member of Nullsoft.
Nullsoft has had its conflicts with AOL in the past, such as in 2000 when Frankel developed a music file-swapping technology called Gnutella. AOL quickly pulled it off the Web fearing legal ramifications, but not before developers downloaded it and began creating services based on its software code.
At this point WASTE is under an open source license at sourceforge.net and is free to the general public.
Thanks to these information sources :
http://waste.globaldisarray.org/
& The WASTE.doc v1.0 from who ever created it.
This guide is dedicated to all the people who have contributed any kind of advancement or betterment of WASTE.
Any comments/ideas/mistakes/things I left out; please don't hesitate to post them at WASTEs source forge site: http://sourceforge.net/projects/WASTE/.